Kicking off with which type of software enables centralized administration of mobile devices, this opening paragraph is designed to captivate and engage the readers, providing an interesting overview of the topic.
The discussion will delve into different software solutions, the importance of centralized administration, key features to look for, implementation best practices, and more.
Types of software for centralized administration of mobile devices
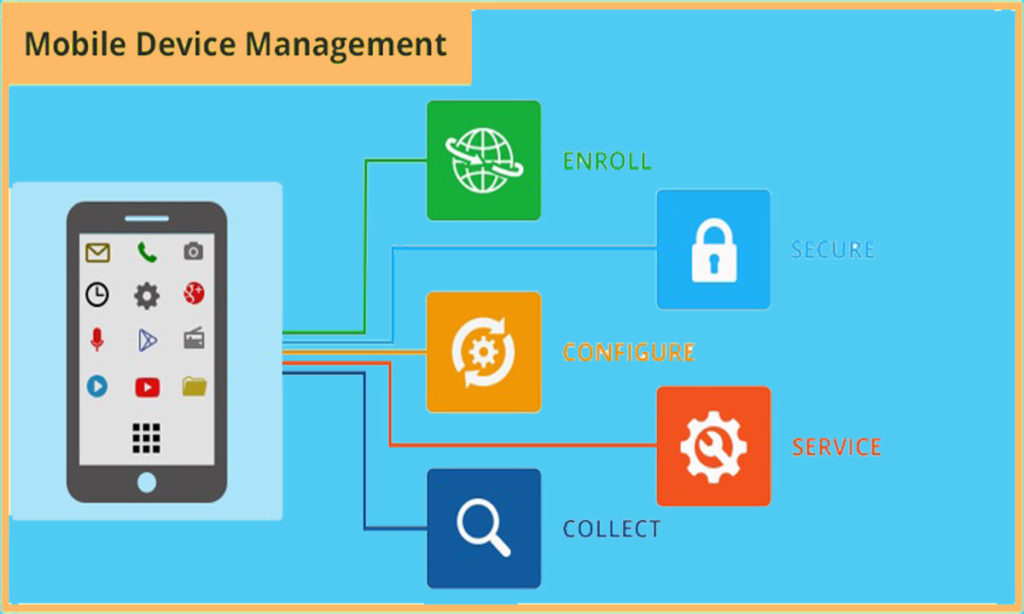
Centralized administration of mobile devices can be achieved through various types of software solutions, each offering unique features and functionalities to manage devices efficiently. Let’s explore some of the common types of software used for this purpose.
Mobile Device Management (MDM)
Mobile Device Management (MDM) software allows IT administrators to remotely control and manage mobile devices such as smartphones and tablets. Key features of MDM software include device configuration, security enforcement, application management, and remote wipe capabilities. While MDM provides comprehensive control over devices, it may be more suitable for company-owned devices due to its intrusive nature.
Mobile Application Management (MAM)
Mobile Application Management (MAM) software focuses on managing and securing mobile applications rather than the entire device. It enables administrators to control app distribution, updates, and security policies. MAM solutions are ideal for organizations that prioritize app management and data security without the need for full device control.
Unified Endpoint Management (UEM)
Unified Endpoint Management (UEM) software combines MDM and MAM capabilities to manage a variety of endpoints, including mobile devices, computers, and IoT devices. UEM offers a holistic approach to device and app management, streamlining IT operations and enhancing security. However, UEM solutions may be more complex to implement compared to standalone MDM or MAM software.
Pros and Cons Comparison
- MDM:
- Pros: Comprehensive device control, security enforcement
- Cons: Intrusive on user privacy, may not be suitable for BYOD environments
- MAM:
- Pros: Focus on app management, data security
- Cons: Limited device control, may not meet all device management needs
- UEM:
- Pros: Holistic endpoint management, streamlined IT operations
- Cons: Complex implementation, potential cost implications
Importance of centralized administration for mobile devices
Mobile devices have become an integral part of daily life and work, making it essential to efficiently manage them. Centralized administration plays a crucial role in streamlining the management of mobile devices, providing numerous benefits such as increased security, improved productivity, and simplified device management.
Efficient Device Management
Centralized administration software allows IT administrators to remotely manage and control multiple mobile devices from a single interface. This centralized approach ensures that software updates, security patches, and configurations can be easily deployed across all devices, reducing the time and effort required for manual management.
Overcoming Challenges
Consistent Policy Enforcement
With centralized administration, IT administrators can enforce consistent security policies and settings across all devices, ensuring compliance with company standards.
Lost or Stolen Device Management
Centralized administration enables the remote wiping of sensitive data from lost or stolen devices, preventing unauthorized access to confidential information.
Application Management
Administrators can easily install, update, or remove applications on all devices simultaneously, ensuring that employees have access to the necessary tools for their tasks.
Enhanced Security and Productivity
Data Protection
Centralized administration helps in implementing encryption, passcode requirements, and secure network configurations, enhancing the security of mobile devices and the data they store.
Monitoring and Reporting
IT administrators can monitor device usage, track compliance with security policies, and generate reports on device status and performance, contributing to improved security and productivity.
Remote Troubleshooting
Centralized administration allows for remote troubleshooting of device issues, reducing downtime and increasing employee productivity by quickly resolving technical issues.
Key features to look for in software for centralized mobile device administration
When selecting software for centralized mobile device administration, there are several key features to consider that can significantly impact the efficiency and effectiveness of managing devices across an organization.
Remote Device Management
- Remote device control and troubleshooting capabilities
- Ability to push software updates and security patches remotely
- Remote lock and wipe functions in case of device loss or theft
Policy Enforcement and Compliance
- Policy creation and enforcement for device usage and security settings
- Compliance monitoring and reporting to ensure devices adhere to organizational standards
Inventory Management
- Automatic inventory tracking of all mobile devices connected to the system
- Real-time visibility into device status, location, and usage patterns
- Alerts for unauthorized or suspicious device activities
App Management
- Centralized app deployment and management
- Ability to blacklist or whitelist specific apps for security and productivity purposes
- Monitoring of app usage and performance metrics
Security Features
- Encryption capabilities for data protection
- Multi-factor authentication for secure access to the management console
- Integration with existing security tools and protocols
Integration and Scalability
- Integration with other IT systems for seamless data sharing and management
- Scalability to support the growing number of devices and users within the organization
Implementation and best practices for deploying centralized administration software
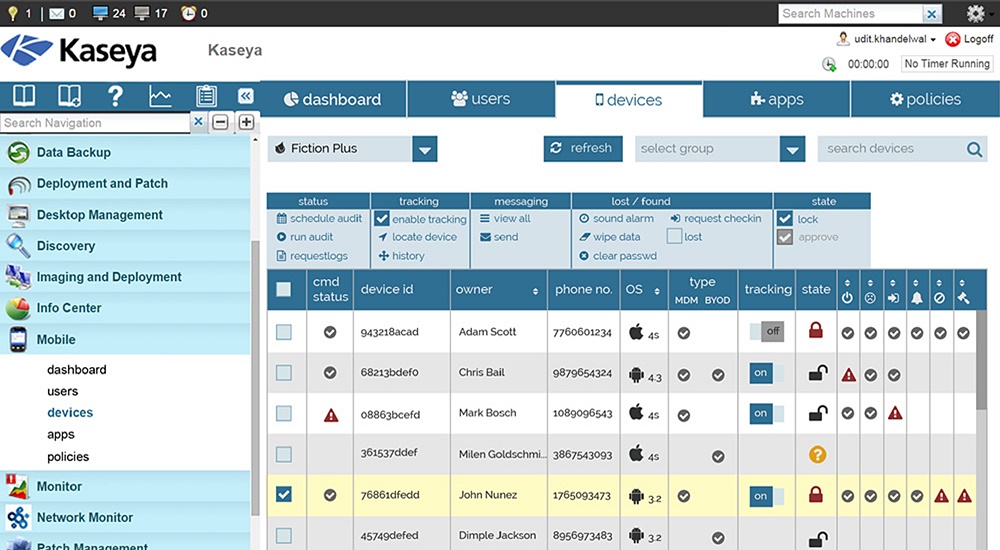
Implementing centralized administration software for mobile devices involves several key steps to ensure a successful deployment and management. By following best practices and being prepared for common challenges, organizations can streamline the process and maximize the benefits of centralized administration.
Steps for implementing centralized administration software:
- Assess organizational needs and requirements for mobile device management.
- Research and select a centralized administration software solution that aligns with the organization’s goals.
- Plan and design the implementation strategy, including defining user roles and access levels.
- Test the software in a controlled environment before full deployment to identify any potential issues.
- Train IT staff and end-users on how to use the software effectively.
- Roll out the software in phases to minimize disruption and ensure a smooth transition.
Best practices for successful deployment and management:, Which type of software enables centralized administration of mobile devices
- Establish clear communication channels with stakeholders to keep them informed throughout the implementation process.
- Regularly monitor and assess the performance of the centralized administration software to identify areas for improvement.
- Implement security protocols to protect sensitive data and prevent unauthorized access to mobile devices.
- Regularly update the software to ensure compatibility with new devices and security patches.
- Provide ongoing training and support to users to maximize the benefits of centralized administration.
Common challenges during implementation and how to overcome them:
- Resistance to change: Address concerns and provide clear rationale for implementing centralized administration software to gain buy-in from stakeholders.
- Integration issues: Work closely with vendors and IT teams to ensure seamless integration with existing systems and applications.
- User adoption: Offer training sessions, resources, and support to help users transition to the new software smoothly.
- Data migration: Develop a comprehensive plan for migrating data to the centralized administration software and conduct thorough testing to mitigate risks.
Final Summary: Which Type Of Software Enables Centralized Administration Of Mobile Devices
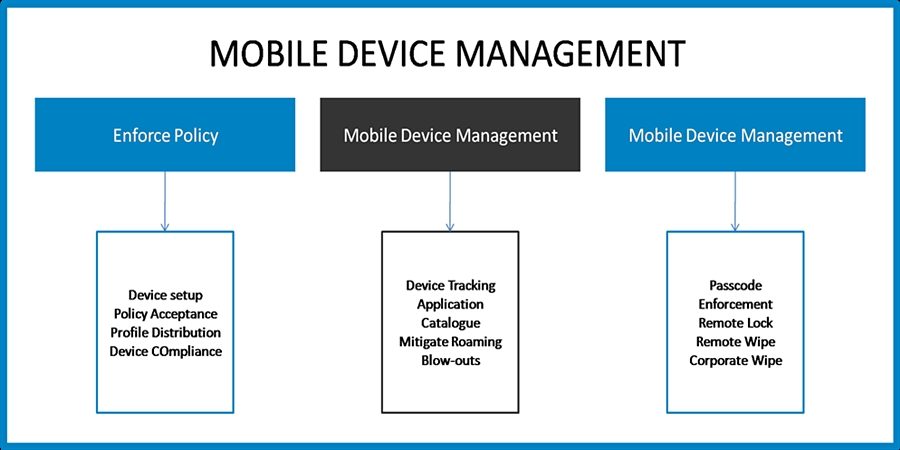
In conclusion, understanding the various types of software available for centralized administration of mobile devices is crucial for effective management and enhanced security.
User Queries
What are the common types of software used for centralized administration of mobile devices?
Common types include Mobile Device Management (MDM) software, Enterprise Mobility Management (EMM) solutions, and Unified Endpoint Management (UEM) platforms.
Why is centralized administration important for managing mobile devices?
Centralized administration ensures streamlined control, security enforcement, and efficient management of mobile devices across an organization.
What are some key features to consider when selecting software for centralized mobile device administration?
Essential features include remote device wipe, app management, security compliance enforcement, and real-time monitoring capabilities.
