Starting with the best encryption software for external hard drive, this introduction delves into the crucial aspects of securing your […]
Category: Uncategorized
Best External Hard Drive Encryption Software: Safeguard Your Data
Best external hard drive encryption software ensures the security of your sensitive data. Discover the top solutions that offer robust […]
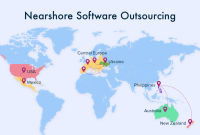
Choosing the Best Nearshore Software Company for Your Project
Nearshore software company brings a unique approach to software development, offering a range of benefits that set them apart in […]
Blacklisting Software: Enhancing Cybersecurity Measures
Blacklisting software plays a crucial role in cybersecurity by identifying and blocking malicious content. Let’s delve into its types, working […]
Hire Offshore Software Developers for Cost-Effective Solutions
Delving into hire offshore software developers, this introduction immerses readers in a unique and compelling narrative, with casual formal language […]
Concise and Clear: Nearshore Software Companies Benefits and Trends
Nearshore software companies offer a unique approach to software development, providing advantages that set them apart from offshore and onshore […]
Software Blacklist: Enhancing Cybersecurity with Effective Filtering
Software blacklist is a crucial tool in cybersecurity, filtering out potential threats to protect systems. Let’s delve into its workings […]
Blacklisted Software: Understanding the Dangers and Solutions
Blacklisted software, encompassing malware, spyware, and adware, poses serious threats to systems worldwide. Let’s delve into the risks, signs, prevention […]
Nearshore Software Testing: Maximizing Efficiency and Quality
Nearshore software testing sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich […]
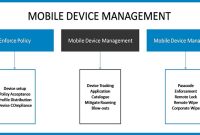
Which type of software enables centralized administration of mobile devices
Kicking off with which type of software enables centralized administration of mobile devices, this opening paragraph is designed to captivate […]