Starting with whitelisting software, this paragraph aims to provide a captivating overview of the topic. Whitelisting software plays a crucial role in enhancing cybersecurity measures by allowing only approved programs and applications to run on a system. Understanding how whitelisting software works and its significance in safeguarding digital environments is essential in today’s cyber threat landscape.
Definition of Whitelisting Software
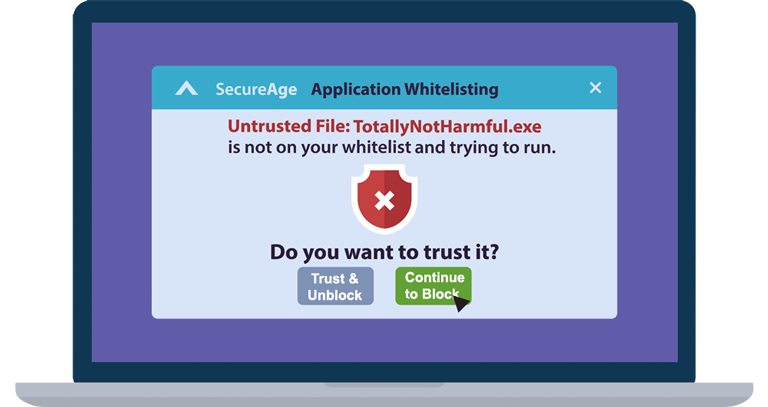
Whitelisting software is a security tool used to control and restrict access to specific applications, programs, or websites on a computer or network. Unlike traditional blacklisting, which blocks known threats, whitelisting only allows approved or trusted entities to run, minimizing the risk of malware infections and unauthorized access.
How Whitelisting Software Works
Whitelisting software works by creating a list of approved applications, files, or websites that are allowed to run or be accessed. When a user tries to execute a program or access a website, the whitelisting software checks if it is on the approved list.
If the entity is not on the whitelist, access is denied, providing an additional layer of protection against potential threats.
Examples of Common Whitelisting Software Programs
- 1. McAfee Application Control: A whitelisting solution that restricts unauthorized applications from running on endpoints.
- 2. Bit9 Security Platform: Provides application control and whitelisting capabilities to prevent untrusted software from executing.
- 3. Carbon Black Protection: Offers endpoint security with application control features, including whitelisting functionality.
Benefits of Whitelisting Software

Whitelisting software offers several advantages in enhancing cybersecurity and protecting systems from potential threats. By allowing only approved applications to run, whitelisting software can significantly reduce the risk of malware infections and unauthorized access.
Enhanced Security Measures
- Whitelisting software provides a proactive approach to cybersecurity by only permitting authorized applications to run on a system.
- It helps prevent the execution of malicious software, such as ransomware, viruses, and other forms of malware.
- By restricting unauthorized software, whitelisting software minimizes the attack surface and strengthens overall security posture.
Improved System Performance
- Since only approved applications are allowed to run, whitelisting software can help optimize system resources and improve performance.
- By reducing the number of unnecessary programs running in the background, whitelisting software can enhance system speed and efficiency.
Real-Life Scenarios
One real-life scenario where whitelisting software proved beneficial is in the healthcare industry. Hospitals and medical facilities often use whitelisting software to ensure that only approved medical applications are running on their systems. This helps protect sensitive patient data and critical healthcare systems from cyber threats.
Implementation of Whitelisting Software
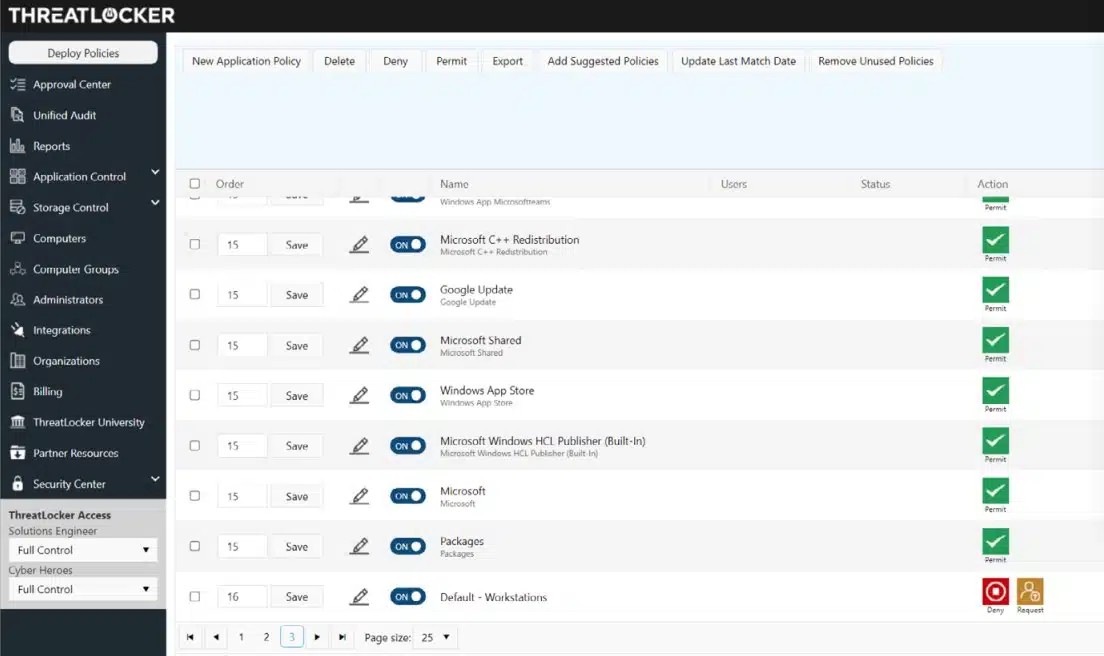
Implementing whitelisting software in an organization involves a series of steps to ensure a smooth deployment and effective configuration. By comparing different methods of integration and discussing best practices, organizations can optimize the use of whitelisting software for enhanced security.
Steps to Deploy Whitelisting Software
- Assess the organization’s needs and determine the scope of whitelisting software deployment.
- Choose the appropriate whitelisting software solution based on the organization’s requirements.
- Plan and schedule the deployment process, considering potential impact on existing systems.
- Install and configure the whitelisting software on all relevant devices and systems within the organization.
- Test the whitelisting software to ensure it is effectively blocking unauthorized applications while allowing approved ones.
- Train employees on how to use and interact with the whitelisting software to maintain security protocols.
- Maintain regular updates and monitoring of the whitelisting software to address any emerging threats or vulnerabilities.
Comparing Methods of Integrating Whitelisting Software
- Agent-based integration: Involves installing software agents on individual devices for granular control over applications.
- Agentless integration: Utilizes existing infrastructure to enforce whitelisting policies without the need for additional software installations.
Best Practices for Configuring Whitelisting Software Effectively
- Define clear whitelisting policies based on business requirements and security protocols.
- Regularly review and update the whitelist to add or remove applications as needed.
- Implement multi-factor authentication for access to whitelist configurations to prevent unauthorized changes.
- Monitor whitelisting software logs for any suspicious activities or attempted breaches.
- Integrate whitelisting software with existing security solutions for a comprehensive defense strategy.
Challenges and Limitations of Whitelisting Software
While whitelisting software offers several benefits, there are also challenges and limitations that organizations may face when relying solely on this approach for security.
Potential Drawbacks of Relying Solely on Whitelisting Software
- Whitelisting can be time-consuming and resource-intensive to set up and maintain, especially in large organizations with a wide range of applications and devices.
- It may be challenging to keep the whitelist updated with new software versions, patches, and emerging threats, leading to potential security vulnerabilities.
- False positives can occur when legitimate applications are mistakenly blocked due to incomplete or inaccurate whitelists, causing disruptions to business operations.
Common Challenges Faced When Using Whitelisting Software
- Resistance from end-users who may find restrictions imposed by whitelisting software intrusive or limiting to their productivity.
- Compatibility issues may arise with certain software applications or devices that are not officially supported by the whitelisting software, leading to gaps in security coverage.
- Complexity in managing exceptions and special cases that require temporary or permanent bypassing of whitelisting rules, adding complexity to the overall security posture.
Strategies to Overcome Limitations of Whitelisting Software
- Regularly review and update the whitelist to include new software versions, patches, and trusted applications while removing outdated or unnecessary entries.
- Implement a robust change management process to ensure that any modifications to the whitelist are properly tested and validated before deployment.
- Provide adequate training and support to end-users to educate them about the benefits of whitelisting software and address any concerns or resistance effectively.
- Monitor and analyze whitelist activity to identify and address false positives promptly, improving the accuracy and reliability of the whitelisting approach.
Closure
In conclusion, whitelisting software offers numerous benefits in bolstering cybersecurity defenses, but it also comes with its set of challenges and limitations. By implementing best practices and strategies, organizations can maximize the effectiveness of whitelisting software to protect their systems from malicious activities.
Questions and Answers
Can whitelisting software prevent all types of cyber threats?
While whitelisting software is effective in blocking unauthorized applications, it may not provide complete protection against all cyber threats. It is crucial to complement whitelisting with other security measures for comprehensive defense.
Is whitelisting software easy to implement?
Implementing whitelisting software can vary in complexity depending on the organization’s IT infrastructure. Proper planning and testing are essential to ensure a smooth deployment process.
